Overview
There are two ways to store configuration information in Checkly: Variables and secrets. Both variables and secrets are encrypted at rest and in flight.- Variables are used to store non-sensitive information. Variables are shown in plaintext when being edited, on the check result page and in logs. Variables can be accessed via the CLI and API.
- Secrets allow you to store sensitive data for use in checks. Once saved, secrets are never shown in the UI or in logs and cannot be accessed via the CLI or API.
Secrets are fully supported starting with runtime version 2024.09 and later. For Private Locations, secrets are available in agent version
3.3.4 and later, and for the CLI, in version 4.9.0 and later.Managing variables
You can create environment variables and secrets at three hierarchical levels:Check-level
Check-level
Variables defined at the check level are only available to that specific check. Use these for check-specific configuration or to override group/global variables.Supported by: API (only via the CLI), Browser, Multistep & Playwright checksCheck-level variables are shown in the Variables tab on the check edit page.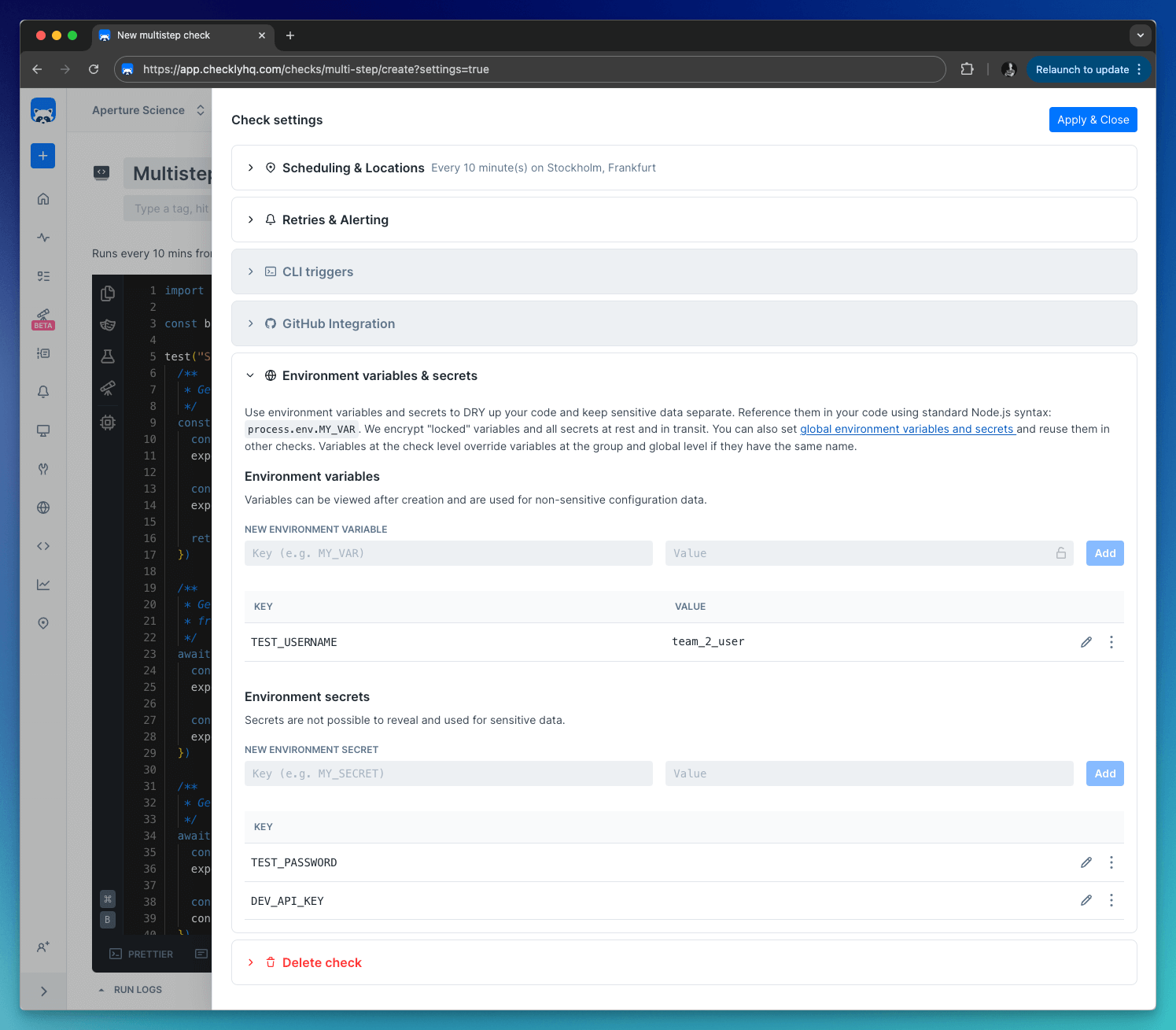

Group-level
Group-level
Group variables are only accessible in the context of a group, which includes the checks within the group and their configuration.Group-level variables are shown the Variables tab in a check group.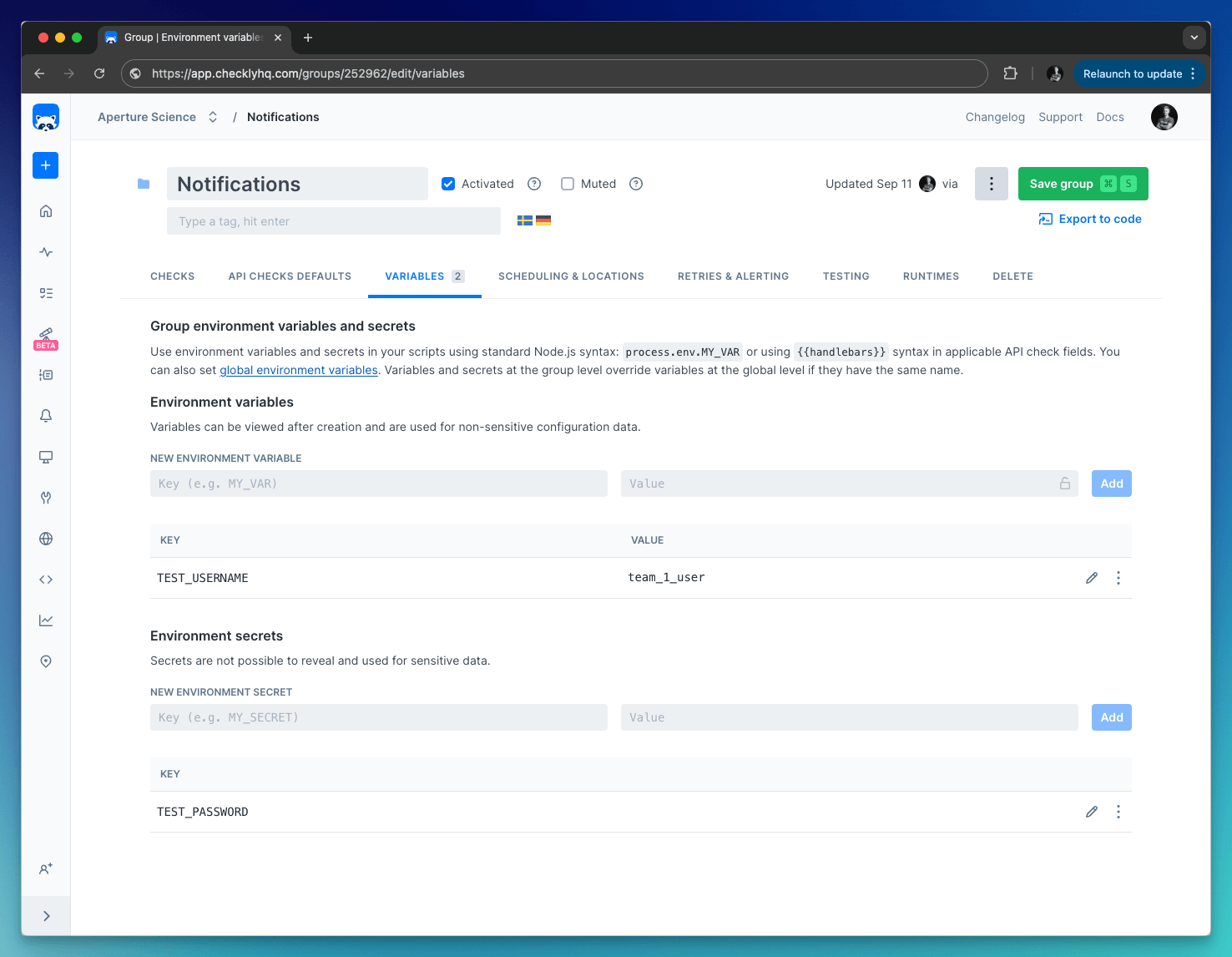

Global
Global
Variables defined at the global level are available throughout Checkly, including in checks, alert channels, and global configuration options.Global variables are shown in the Environment variables section on the left-side menu.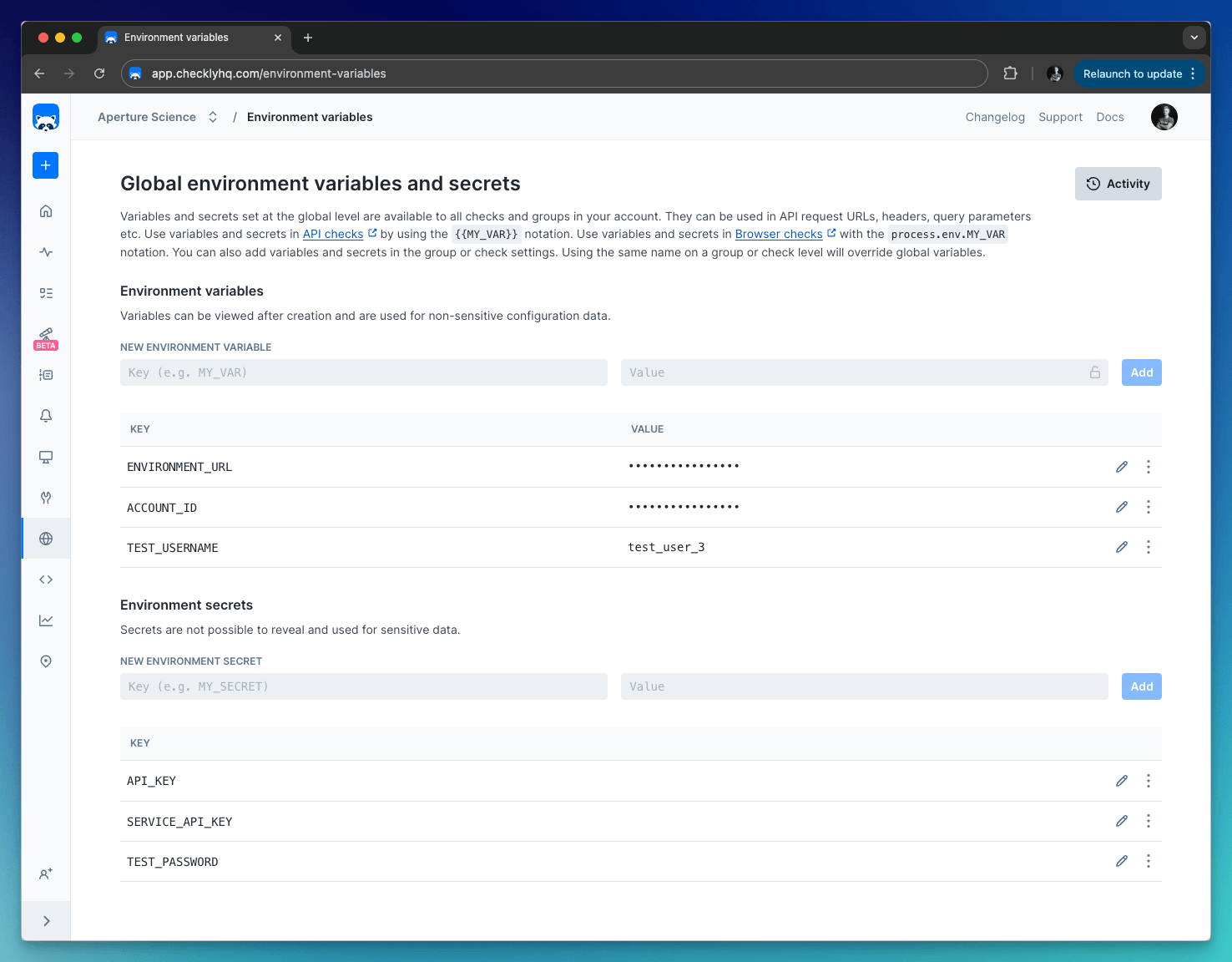

Store variables at the global level whenever possible to follow the DRY (Don’t Repeat Yourself) principle.
Variable hierarchy
As checks are scheduled, Checkly merges the check, group, and global environment variables into one data set and exposes them to the runtime environment. During merging, variables at more specific levels override those at broader levels. Or, in other words: check variables override group variables override global variables. You can make use of this by providing a default value for a specific variable at the global or group level, but allow that variable to be overridden at the check level.Accessing variables
How variables are accessed depends on where you’re accessing them from:- In Browser, Multistep, and API Check setup/teardown scripts, use the standard Node.js
process.env.VARIABLE_NAMEnotation. - In API Check requests, use Handlebars/Moustache templating delimiters, i.e.
{{VARIABLE_NAME}} - In webhook alert channels, also use the Handlebar/Moustache format, i.e.
{{VARIABLE_NAME}}
Handlebar (double brackets) variables will be URI encoded. To avoid encoding, you can access your environment variables with triple brackets, i.e.
{{{VARIABLE_NAME}}}.